Greetings!
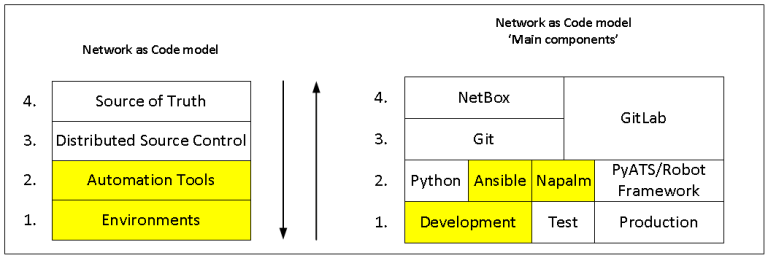
In this post, I will show the ‘Main components’ of NaC model such as Ansible and NAPALM more deeply.
If you have not read the ‘Introduction’ post, it is a good starting point to understand what I will talk about.
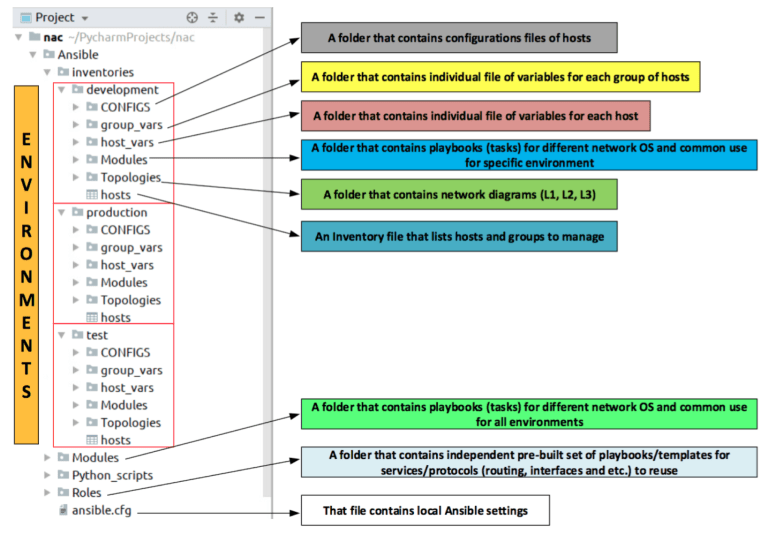
One of the main tools for working with the network is PyCharm CE that contains the project (nac) which I will use to configure the network of company ‘X’ but before I will start to configure, I want to show Ansible and NAPALM how they work together using simple examples.
Ansible
In order not to write about the same thing, I leave links to useful resources:
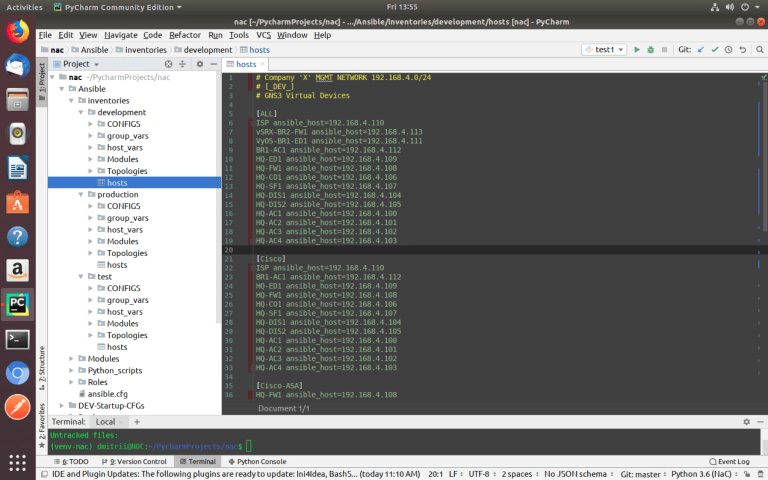
The value in [__] is a group, for example, [Cisco] where all hosts are Cisco network devices and have a network OS — Cisco IOS.
Next, that is a simple example of ansible playbook (ping.yaml) which will use to check the availability of devices from the ‘hosts’ file.
ansible-playbook –i inventories/development/hosts inventories/development/Modules/PING/ping.yaml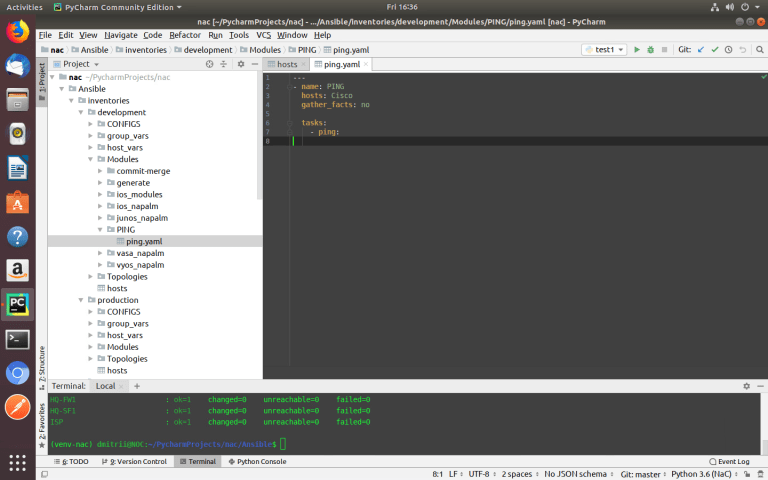
---
- name: PING # play name
hosts: Cisco # run tasks on that group of devices
gather_facts: no # do not collect data for variables
tasks:
- ping: # module name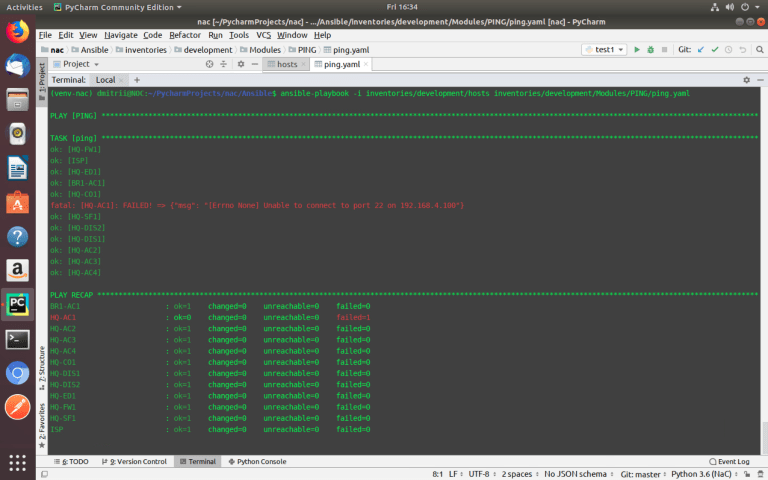
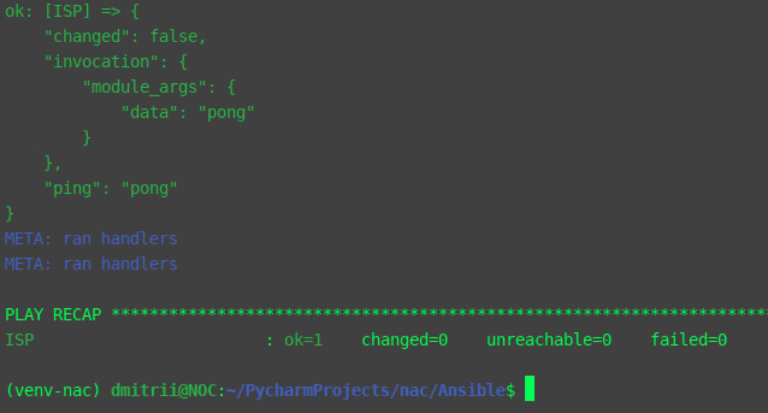
You can see that all devices except ‘HQ-AC1’ are available via SSH.
https://docs.ansible.com/ansible/latest/modules/ping_module.html
Ansible establishes SSH connection to the devices using ‘paramiko SSH’
https://docs.ansible.com/ansible/latest/plugins/connection.html
Ansible uses ‘SSH’ primarily for the transport.
I can use a verbose logging (-vvvvv) to see more detailed information about ansible playbook that is useful for debugging playbooks.
–limit ‘ISP’ – runs that playbook only for ‘ISP’ device.
ansible-playbook –i inventories/development/hosts inventories/development/Modules/PING/ping.yaml --limit ISP -vvvvv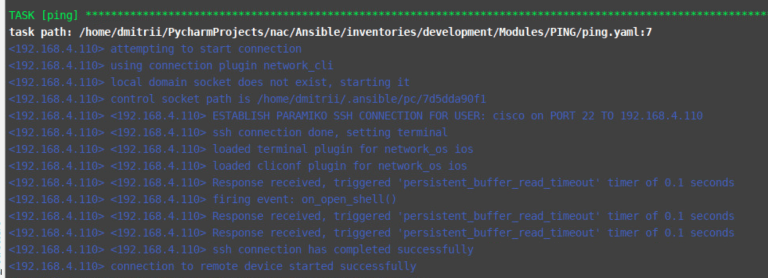
To connect via SSH, Ansible needs ‘username’ and ‘password’ for a specific device. Ansible takes that data from variables, for example:
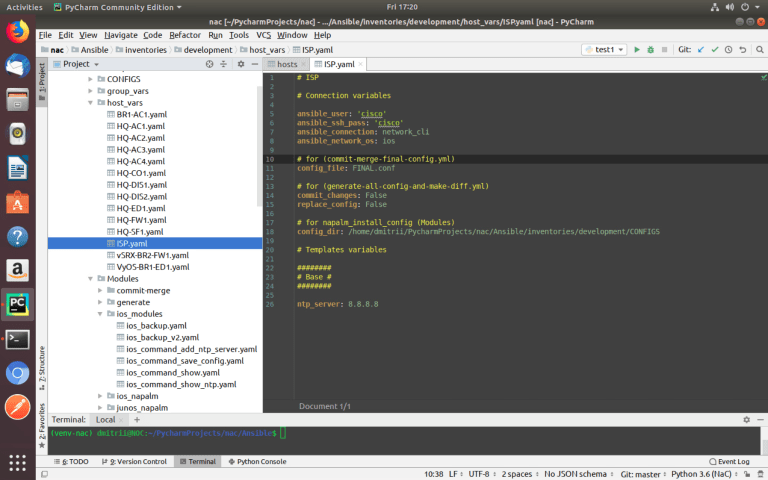
# Connection variables
ansible_user: 'cisco'
ansible_ssh_pass: 'cisco'
ansible_connection: network_cli # connection plugin
ansible_network_os: ios # NAPALM driverhttps://docs.ansible.com/ansible/latest/plugins/connection/network_cli.html

Of course, that is NOT secure, it is all in the plain text!
The best practice is to use the SSH public/private key pair.
For simplicity, I will leave login and password in the plain text, but later, I will replace connection type to SSH key-pair.
Another option is to use Ansible Vault:
https://docs.ansible.com/ansible/latest/user_guide/vault.html
Also, the variables that are described in ‘host_vars/device.yaml’ will use to create device configuration files using ‘Roles’ and ‘Jinja2 templates’ which I will show in the next posts.
NAPALM
https://github.com/napalm-automation/napalm
Example of use:
Supported devices:
https://napalm.readthedocs.io/en/latest/support/index.html
Community drivers:
https://github.com/napalm-automation-community
I am using a set of modules for Ansible – ‘napalm-ansible’
https://github.com/napalm-automation/napalm-ansible
The main ones are:
- napalm_get_facts
- napalm_install_config
NAPALM drivers which I use for the project:
- ‘ios’
- ‘junos’
- ‘asa’ – community driver (REST API)
- ‘vyos’ – community driver
Caveats of Cisco IOS:
https://napalm.readthedocs.io/en/latest/support/ios.html
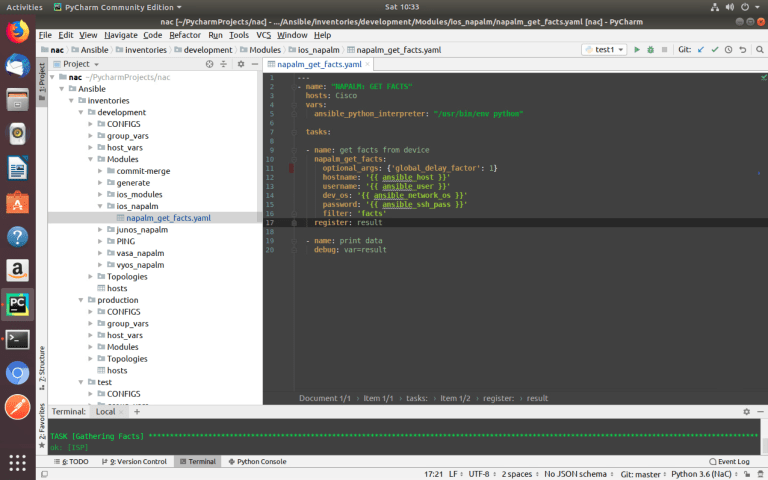
ansible-playbook –i inventories/development/hosts inventories/development/Modules/ios_napalm/napalm_get_facts.yaml –-limit ISP---
- name: "NAPALM: GET FACTS"
hosts: Cisco
vars:
ansible_python_interpreter: "/usr/bin/env python"
tasks:
- name: get facts from device
napalm_get_facts:
optional_args: {'global_delay_factor': 1}
hostname: '{{ ansible_host }}'
username: '{{ ansible_user }}'
dev_os: '{{ ansible_network_os }}'
password: '{{ ansible_ssh_pass }}'
filter: 'facts'
register: result
- name: print data
debug: var=result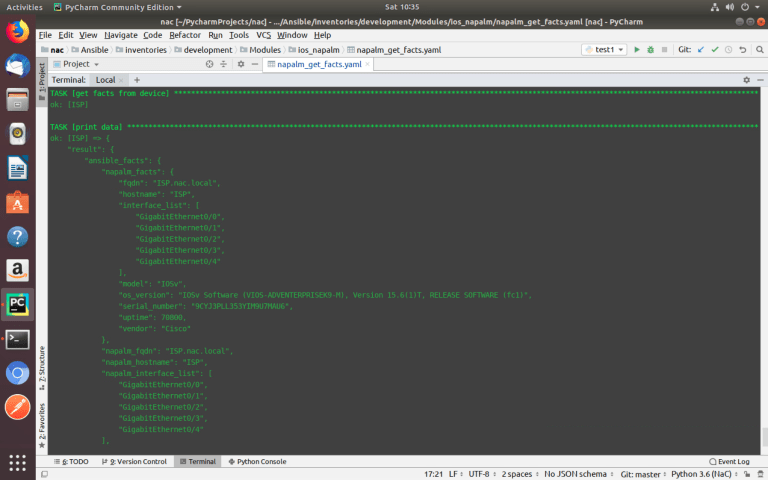
Using variables and NAPALM module ‘get_facts()’, you can collect data about all devices of different vendors using one universal Ansible playbook.
Variables are located in the ‘host_vars’ directory for each device in the separate file.
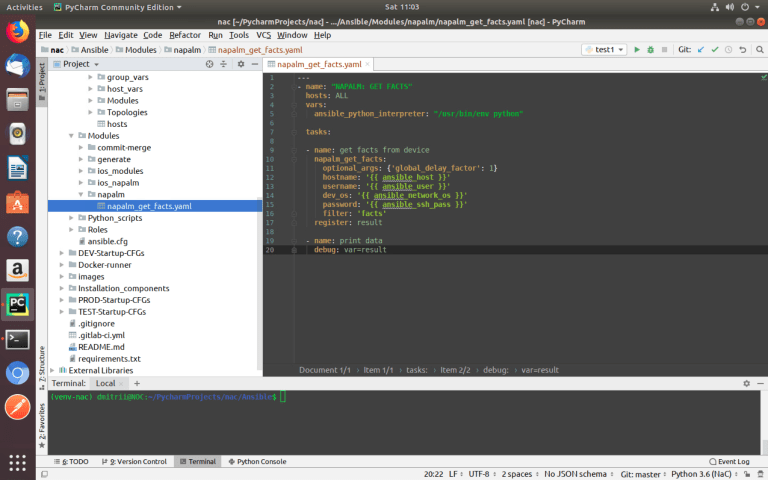
ansible-playbook –i inventories/development/hosts Modules/napalm/napalm_get_facts.yaml –-limit ISP,vSRX-BR2-FW1,VyOS-BR1-ED1,HQ-FW1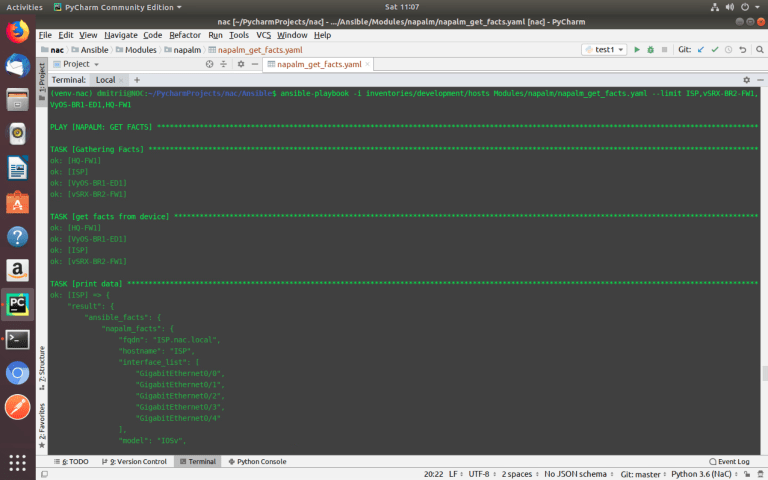
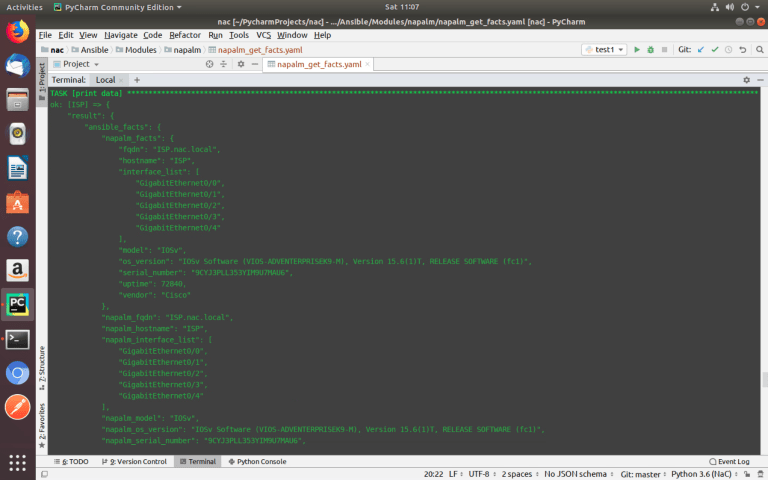
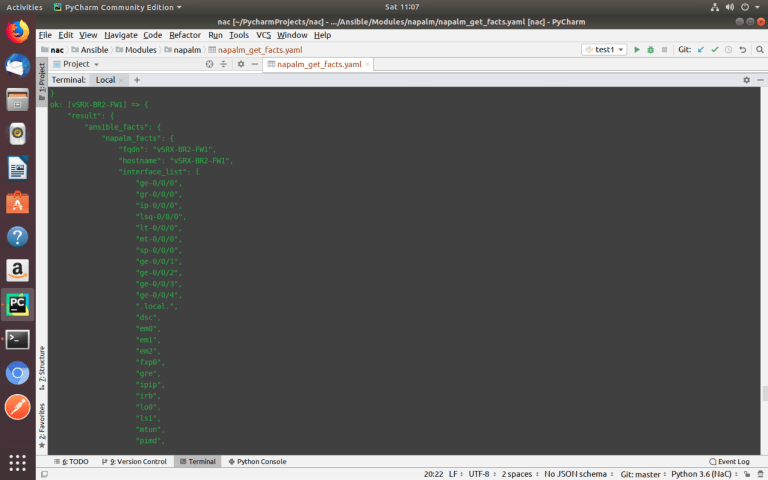
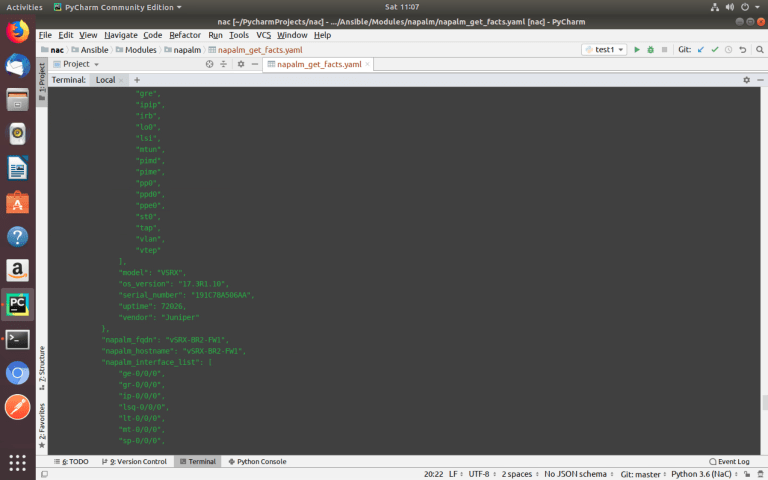
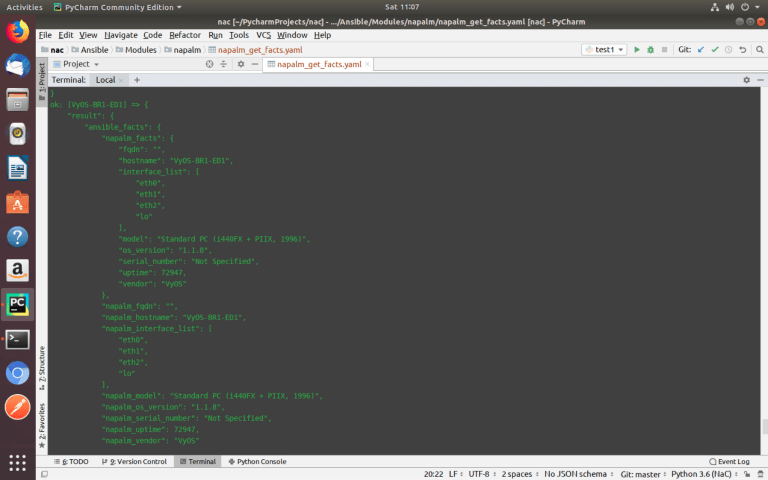
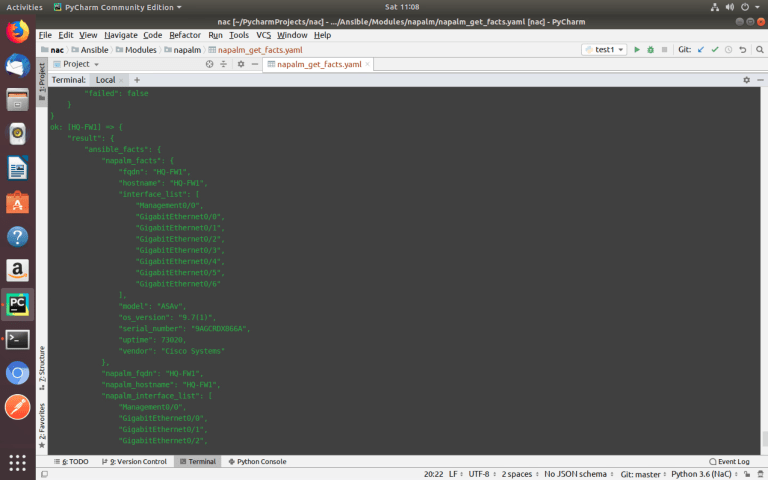
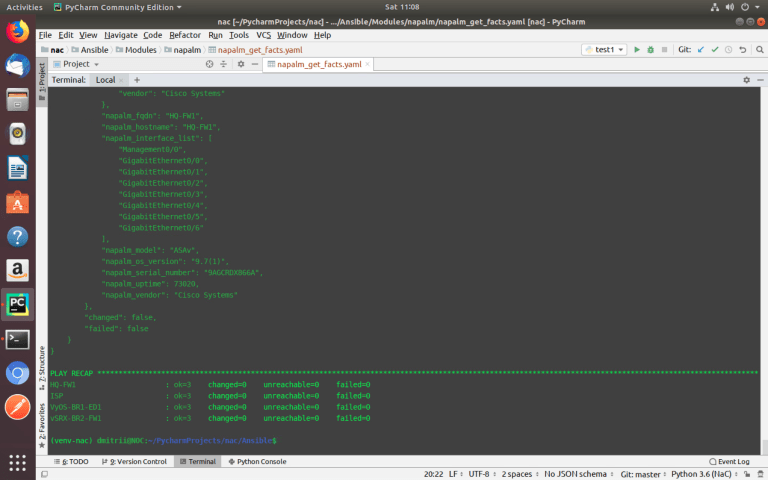
To know what data can be collected, you need to look at
‘Support matrix table’ for each vendor:
https://napalm.readthedocs.io/en/latest/support/index.html
P. S. At the end of the project, I will make my GitHub repository public that where the project files are located (startup configurations, ansible playbooks, docker-compose.yml and etc.)